
Challenge
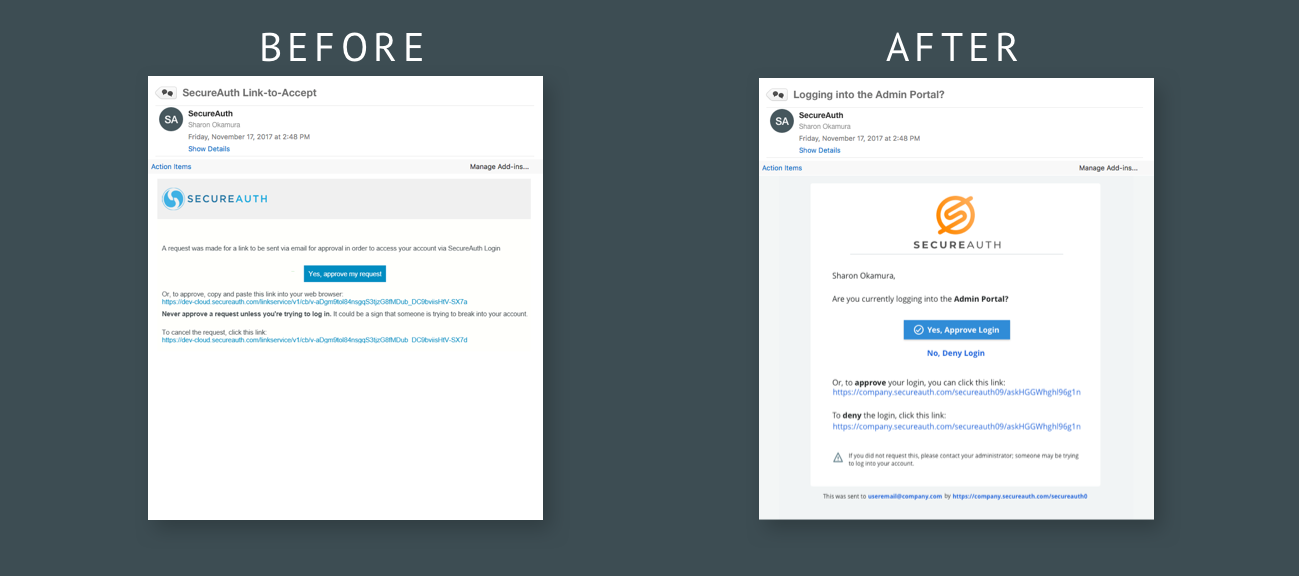
The wording. The default experience included industry terms such as “OTP” or “login request” that confused and undermined end user confidence.
The wording was also inconsistent within the login experience itself
It was so difficult to understand that many companies customized the verbiage
We also could not remove or change any of the verbiage originally built in with the product, as it would have rippling effects over customizations and translations
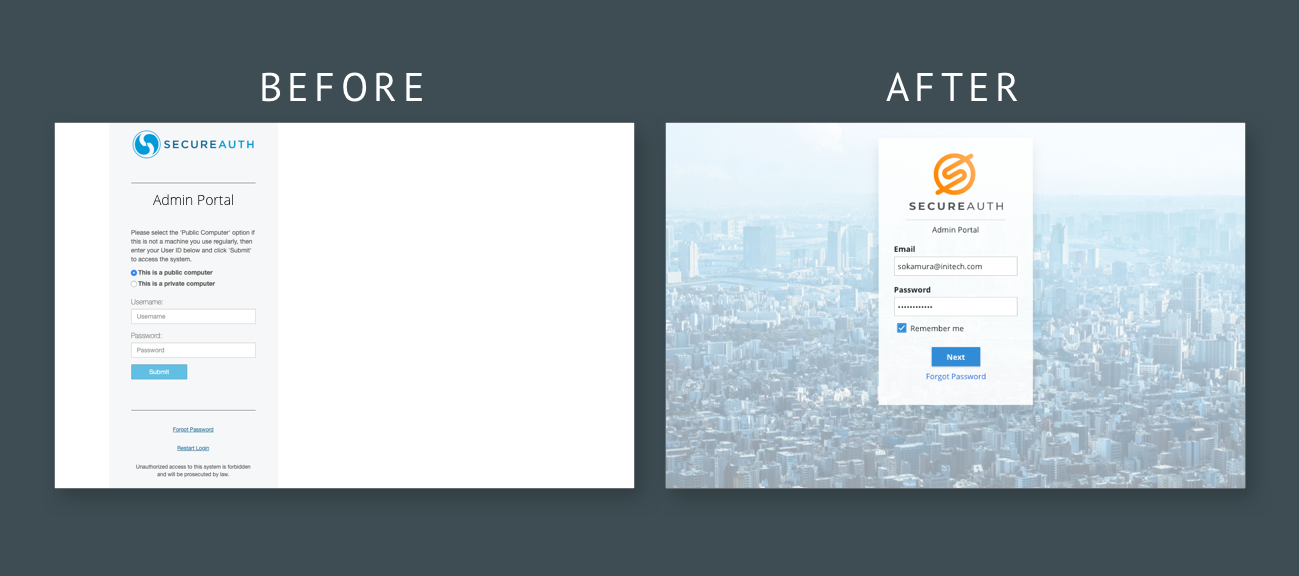
The branding. Our customers liked to have their login experience reflect their own company’s brand. In the legacy experience, this either requires our customer to pay a premium for us to brand it for them, or they have to muck around our code and do it themselves, which has ambiguous security consequences.
my role
When I was tasked with redesigning the legacy login experience, it was under the assumption that the product was going to be completely re-architected, allowing me much more freedom with the design and wording.
As SecureAuth’s business is in login security and authentication, this login experience is foundational to their their entire product suite, which includes desktop applications, mobile, and web.
A glimpse of one of SecureAuth’s popular login themes before the redesign
Process
Internal Research & CompARATIVE Analysis
I took inventory and conducted internal interviews to gain a better understanding of:
the current state of our login experience
its capabilities
its most common configurations
I also looked at competitors and a number of different authentication flows from other services.
User Interviews
One of the major challenges is having two to three degrees of separation between the UX team and the end user.
End users for SecureAuth are our customer’s customer or our customer’s employee. Because we are security software, customers are generally not forthcoming with allowing us to talk to their users about their experience using SecureAuth.
I used UserTesting.com’s Live Conversation feature to conduct in-depth interviews with people who very closely resembled our actual users.
Personas and Journey Maps
I mapped out the traits of our users and grouped common behavior patterns, and four distinct personas emerged.
I also synthesized the data gleaned from the research and created end user journey maps. This is the first time SecureAuth has had such formal, research-backed UX documentation.
Testing & Iteration
Another challenge at SecureAuth is that we do not have metrics on the usage or configurations of our product. This is particularly troublesome when a new design is introduced and adopted; we have no idea how the design is being received.
To ensure that any new designs would be an improvement, I tested our legacy login experience to establish a baseline.
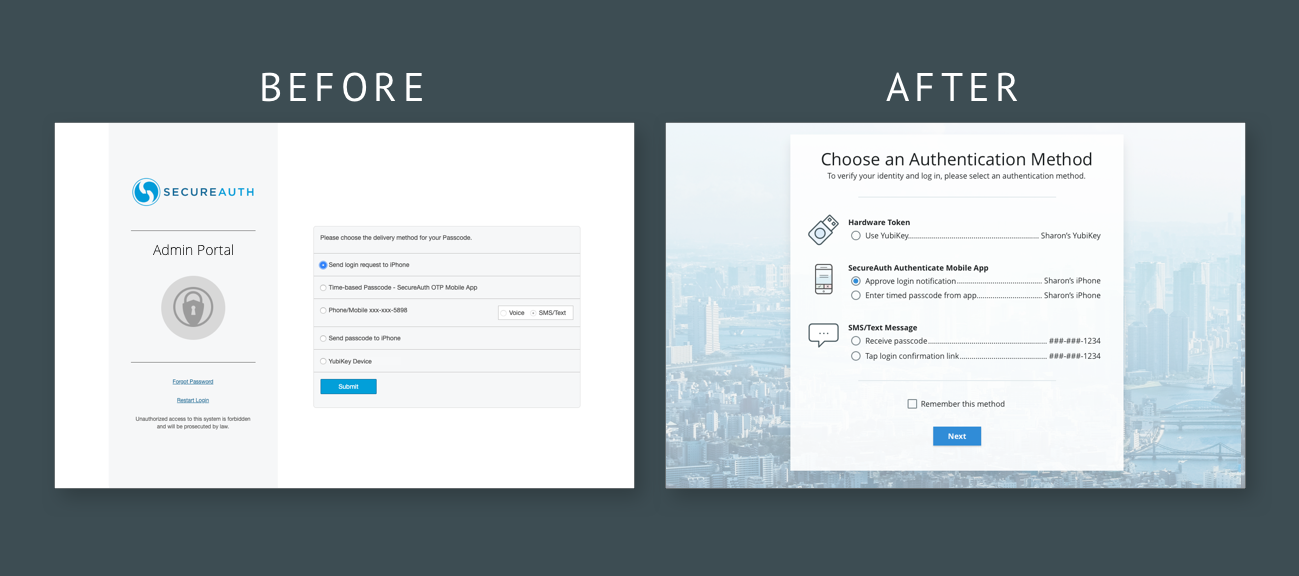
As expected, users were confused about the inconsistency of the wording, as well as industry terms such as “OTP” and “login request”
This resulted in low confidence in selecting those authentication methods
Users also found the organization of authentication methods confusing and difficult to scan
I tested and iterated a number of different options for verbiage and design. The final design allows for:
Easier scanning due to better organization of methods
Clearer wording
Visual cues for what an authentication method might entail.
The legacy 2FA method “pick list.”
Designs & Outcomes

Customer Branding
One of the goals of the login experience was to also allow our customers to more easily brand it, so that they would not have to pay extra or risk their company’s security to try to brand it themselves.
I worked with my colleague Julia Itani to create a new branding experience.
Developer Collaboration
Unfortunately, due to changing requirements, the end user experience I created could not be implemented in its original intended form, but the redesign still needed to be done. I collaborated with our international front end developers and QA to resolve the design.
During sprint demos, I discussed the compromises that had to be made to the user experience.
END TO END AUTHENTICATION EXPERIENCE
Although the design could not be deployed as intended across all SecureAuth products, it is foundational to offering an overall better end-user experience for:
SecureAuth Identity Platform Application and SSO login
SecureAuth endpoint security software for Windows and Mac
SecureAuth desktop Passcode app
SecureAuth Authenticate mobile app for iOS and Android, including Apple Watch and Android Wear